SAN FRANCISCO, Jan. 15, 2026 /PRNewswire/ — 2025 has been a year of rapid evolution for Web3 infrastructure. As a pioneer in AI-driven digital asset security, BitsLab has safeguarded Web3 infrastructure through audits, penetration testing, and continuous security monitoring. To date, they have provided security for 716 million users worldwide and protected over $160 billion in on-chain value.
With its three specialised brands—MoveBit, ScaleBit, and TonBit—BitsLab demonstrated exceptional security prowess in 2025. The firm not only maintained absolute dominance in Move ecosystems such as Sui and Aptos but also established extensive security deployments across mainstream ecosystems like BSC, Ethereum, Solana, TON, and BTC, as well as emerging L1/L2 sectors including Monad, IOTA, Supra, and CKB, building a comprehensive AI security defence matrix.
2025 Core Audit Landscape: AI-Driven Multi-Chain Progress & Full Ecosystem Coverage
In 2025, BitsLab completed 204 audit projects. This achievement not only highlights BitsLab’s deep involvement in mainstream public chains and emerging tracks but also marks BitsLab’s official entry into the ‘AI + Security’ era.
AI Empowerment: Deep Synergy Between BitsLabAI Scanner and Expert Audits
During the 204 project audits, BitsLab fully upgraded its audit paradigm by introducing an AI-driven security system centred on the BitsLabAI Scanner. Based on models trained on massive real-world vulnerability data, the AI performs automated, high-coverage risk screening. This is then combined with AI-assisted formal verification and advanced penetration testing, with final deep-dive audits and judgments completed by expert teams. This provides security for projects with a cumulative TVL exceeding $164 billion, evolving auditing from a one-time delivery into an ‘AI + Expert’ collaborative intelligent defence.
Core Chain Audit Distribution: AI Defence Lines for High-Value Ecosystems.
Among the 204 projects, major public chains represent the core proportion, reflecting the high recognition of BitsLab’s AI security technology in high-value ecosystems:
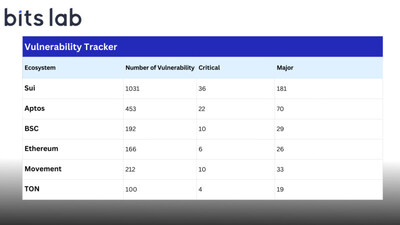
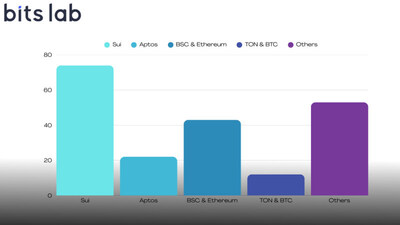
- Move Ecosystem Core (Sui & Aptos): 96 projects audited (74 for Sui, 22 for Aptos), continuing to consolidate absolute dominance in this track.
- Mainstream EVM Ecosystem (BSC & Ethereum): 43 projects audited (31 for BSC, 12 for Ethereum), utilising BitsLabAI Scanner to effectively handle complex logical risks in EVM.
- Value-Store Ecosystems (TON & BTC): 12 projects audited (6 for TON, 6 for BTC), extending the AI security boundary to both emerging and classic value chains.
Extensive Cross-Chain Footprint: One-Stop AI Security Protection Beyond the core chains mentioned above, BitsLab’s AI security reach extends to dozens of other chains, including Solana (4), IOTA (4), EVM Chains (2), CKB (2), Monad (1), DuckChain (1), Starknet (1), and Arbitrum (1). Through the rapid adaptation of the BitsLabAI Scanner, BitsLab achieved efficient security responses in cross-chain environments, truly ‘auditing, monitoring, and defending’ every piece of infrastructure.
Vulnerability Mining Results: AI Scanning + Expert Review Neutralises 2,858 Security Risks
Vulnerability Severity Breakdown: Utilised AI-assisted auditing to precisely locate a massive number of critical risks, effectively defending against potential economic attacks:
- Critical: 101
- Major: 399
- Medium: 661
- Minor/Informational: 1,697
Key Ecosystem Vulnerability Details: Performance of the AI Defence Line. Through the wide application of the BitsLabAI Scanner, BitsLab achieved significant results across major ecosystems:
Brand Matrix: A Triple AI Security Barrier
- MoveBit: The ‘AI Guardian’ of the Move Ecosystem. As the benchmark for Move security, MoveBit uses AI to monitor full-spectrum security across Sui and Aptos, fixing over 1,480 hidden vulnerabilities in 2025.
- ScaleBit: The AI Bridge Connecting EVM and the Future. ScaleBit successfully applied AI auditing to multi-chain environments, including BSC, Ethereum, Solana, and BTC, ensuring the security of complex cross-chain applications under economic pressure and extreme conditions.
- TonBit: The Primary Security Assurance Provider for the TON Ecosystem. As a TON official-certified Primary Assurance Security Provider, TonBit focuses on the rapidly growing TON ecosystem. Through AI scanning and attack simulation, it has built an unbreakable security foundation for TON protocols.
Strategic Upgrade: BitsLab Safe Builds a Full-Scene Anti-Phishing and Anti-Fraud Defense
In 2025, BitsLab successfully acquired the well-known Japanese security plugin KEKKAI and rebranded it as BitsLab Safe. This move extends BitsLab’s security capabilities from back-end code logic to front-end interaction protection, building a full-spectrum security matrix ‘from code logic to asset interaction.’
- AI-Driven Real-Time Protection: BitsLab Safe integrates AI transaction simulation and phishing detection to warn of potential risks before a transaction is executed.
- Empowering Agent Security: As the entry point to the BitsLab intelligent security stack, BitsLab Safe secures payment flows for x402 and AI Agents.
In 2025, through the precise neutralisation of 2,858 vulnerabilities and the rigorous protection of $160 billion in assets, BitsLab continues to defend the Web3 industry ecosystem. From deep protocol-level audits empowered by BitsLab AI Scanner to the strategic entry into interaction-side anti-phishing and anti-fraud protection with BitsLab Safe has successfully built a comprehensive security matrix ‘from underlying code to terminal interaction, and from protocol logic to asset flow.’
In the coming era of interconnected chains and the accelerated AI Agent economy, BitsLab will continue to deepen its presence in the multi-chain ecosystem and iterate on AI security technology. With ‘Audit, Monitor, and Defend’ as their core mission, BitsLab defines the new security standards for the Web3 era, ensuring that every bit of value in the decentralised world can circulate freely under the protection of AI and industry experts.
About BitsLab
BitsLab is an AI-driven security company focused on digital asset protection. It delivers an integrated solution of ‘audit services + AI security engine + security tools’ for emerging Web3 ecosystems, helping developers and end users build, trade, and interact on-chain with greater safety.
Within its security framework, BitsLab combines BitsLab AI Scanner and BitsLab Safe to form a complete AI-powered protection system. BitsLab Safe, an AI-based Web3 security product, provides enterprise-grade defence by simulating transactions in real time, detecting scams and malicious contracts, and securing x402 payments and AI Agent operations through BitsLab’s agentic security stack. BitsLab AI Scanner, built on a vulnerability and threat intelligence engine, performs intelligent auditing and risk detection to improve efficiency and reduce false positives.
BitsLab operates three sub-brands – MoveBit, ScaleBit, and TonBit-serving emerging ecosystems in Web3. The team offers professional audits and vulnerability research to keep core infrastructure secure during rapid iteration. Its researchers have won multiple international CTF awards and discovered critical vulnerabilities in many major ecosystems, driving meaningful improvements in industry-wide security.
Contact
Marketing Manager
Jason Li
BitsLab
jasonlee@bitslab.xyz
Photo: https://mma.prnewswire.com/media/2862551/BitsLab_Tracker.jpg
Photo: https://mma.prnewswire.com/media/2862552/BitsLab_Graph.jpg
Photo: https://mma.prnewswire.com/media/2862553/BitsLab_2025_Audit.jpg
 View original content to download multimedia:https://www.prnewswire.com/news-releases/bitslab-2025-audit-annual-summary-200-projects-audited-2-858-vulnerabilities-discovered-302662215.html
View original content to download multimedia:https://www.prnewswire.com/news-releases/bitslab-2025-audit-annual-summary-200-projects-audited-2-858-vulnerabilities-discovered-302662215.html
SOURCE BitsLab
![]() View original content to download multimedia:https://www.prnewswire.com/news-releases/zeni-launches-ai-powered-treasury-solution-302662484.html
View original content to download multimedia:https://www.prnewswire.com/news-releases/zeni-launches-ai-powered-treasury-solution-302662484.html